Spyware is a type of software that secretly installs itself on your device and monitors what you do. It collects data about your activity and sends it to third parties without your permission.
Whether you use a smartphone, tablet, or computer, understanding spyware’s meaning and how to protect yourself is important.
Key Takeaways
- Spyware is malicious software that secretly collects information from your device and sends it to others.
- It often gets onto devices through phishing emails, unsafe or compromised websites, software bundles, and fake or malicious apps.
- You can reduce your risk by using trusted security software, updating your device, and being careful about what you click, download, and install.
Spyware: Definition
Spyware is a type of malware (malicious software) designed to gather information from your device without proper notice, consent, or control. Its main goal is to monitor your activity and send data to another person, company, or group.
Once installed, spyware can:
- Track which websites you visit and what you search
- Record what you type, including passwords and card details
- Read browser data such as cookies and saved logins
- In some cases, monitor emails, messages, and files
The stolen data may be used to steal money, take over your accounts, build detailed profiles about you, or sell your information to other parties. Spyware usually does not copy itself like a virus or worm. Instead, it focuses on staying hidden and collecting data over time. According to a recent cybersecurity report, 48% of all successful cyberattacks against individual users involved spyware. This shows how common and effective it is as an attack method.
How Spyware Works
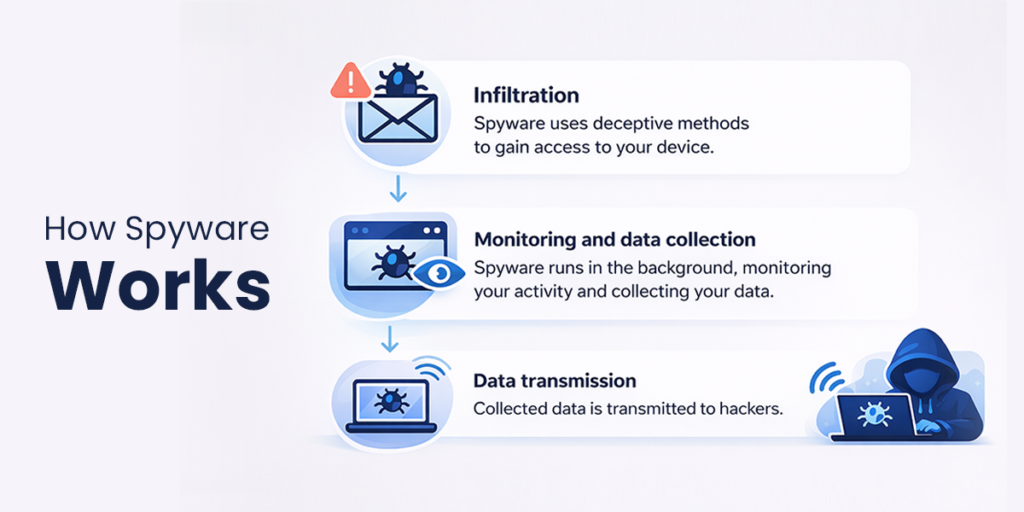
Infection: Spyware first installs itself on your device, often hidden inside other software or apps, through harmful links or email attachments, unsafe websites, or by exploiting security flaws. In advanced attacks, it can use one-click or zero-click methods that require little or no action from you.
Monitoring: After it is installed, spyware runs in the background and watches what you do. It can record what you type, track websites you visit, read browser history and cookies, and look for saved passwords and payment details. On mobile devices, it may also track location, read messages, view call logs and contacts, and use the microphone or camera.
Data Transmission and Persistence: Spyware then sends the collected information over the internet to a server controlled by the attacker, usually without any visible sign. It often changes system or browser settings so it starts automatically, stays hidden, and is harder to remove.
Types of Spyware
Spyware is not one single tool. It is a group of related threats that focus on tracking, stealing, or controlling. Below are the main types you should know.
Adware
Adware is software that displays ads on your device, such as pop-ups or extra banners in web pages. On its own, showing adverts is not always malicious. It becomes a spyware problem when adware:
- Tracks your browsing behaviour in detail
- Sends that data to third parties without proper consent
- Installs or runs without a clear choice
Adware can slow down your device, change your browser settings, and fill your screen with unwanted ads.
Infostealers
Infostealers are spyware programs designed to steal information already stored on your device. They typically look for:
- Saved usernames and passwords
- Browser cookies and session tokens
- Credit card and payment details
- Autofill data from browsers
The stolen data is sent to the attacker, who can then log into your accounts, move money, make purchases, or sell your information to others.
Keyloggers
Keyloggers record every key you press. They can capture:
- Logins and passwords
- Card numbers and PINs
- Email content and chat messages
- Any other text you type
Keyloggers usually run silently and are difficult for ordinary users to notice. They are often delivered by Trojans or other malware, or installed by someone misusing a shared device. Because they see everything you type, they are one of the most dangerous forms of spyware.
System Monitors
System monitors track a wide range of activity on a device. They may:
- Log which applications you open
- Record which websites you visit
- Track how long you use certain apps
- Take screenshots or record clipboard content
System monitoring software is not always harmful. In some workplaces or homes, it is used openly to check device usage, and people are clearly told that monitoring is taking place. In that case, it is part of an agreed policy. However, if similar software is installed in secret or used to track someone without their knowledge or consent, it is generally considered spyware or stalkerware.
Rootkits
Rootkits are advanced programs that hide deep inside the operating system and give attackers a high level of control over the device. They are not always spyware on their own, but they are often used together with spyware to:
- Hide files and processes
- Interfere with security software
- Help spyware survive reboots and removal attempts
Because of their position in the system, rootkit-based infections can be very difficult to remove and sometimes require a full reinstall of the operating system.
Trojan Horses
A Trojan horse (or Trojan) is a program that appears harmless or useful but actually contains malicious code. It might look like a game, utility, or document. When you run it, it installs spyware or other malware in the background.
Trojans are one of the main delivery methods for spyware, including infostealers and keyloggers. While technically a separate category of malware, they are strongly linked to spyware because they are used to place it on devices.
Browser Hijackers
Browser hijackers are programs that attach themselves to your web browser and change its settings without your knowledge or agreement. They are usually installed together with other software or through unsafe downloads and quickly start to interfere with how you browse.
A browser hijacker can:
- Change your homepage
- Replace your default search engine
- Redirect your searches to specific websites
- Add toolbars or extensions that you did not choose to install
In many cases, browser hijackers also track what you search for and which websites you visit, so they can collect data about your browsing habits. Because they change your browser settings without your consent and monitor your online activity, they are often classified as a type of spyware.
Tracking Cookies
Tracking cookies are small text files that websites and advertising networks store in your browser. They are used to recognise you and follow your activity across multiple sites.
Tracking cookies are not executable programs and are not malware in the strict sense. However, they can be used to build detailed profiles of your interests and behaviour and share these with third parties. Many security products therefore mark them as a low-level privacy risk or “spyware-like” item.
Mobile Spyware (Stalkerware)
Mobile spyware targets smartphones and tablets. When it is used to secretly monitor a partner, family member, or other individual, it is often called stalkerware. It can:
- Track your location in real time
- Read SMS messages and some app messages
- View call logs and contacts
- Access photos and files
- Turn on the microphone or camera
In 2023, 31,031 mobile users worldwide were found to have stalkerware on their devices, which is a 5.8% increase compared to the previous year. This shows that mobile spyware is a real and growing problem.
How Spyware Gets on Your Device
Spyware usually relies on user actions or weak security to get onto a device. Common paths include:
Phishing Emails
Phishing emails look as if they come from trusted organisations such as banks, delivery services, government offices, or people you know. They often ask you to click a link or open a file.
The link may take you to a fake or infected website, and the attachment may contain hidden code that uses a weakness in your software. If you follow the link or open the file, spyware can be installed without any clear warning.
Malicious or Compromised Websites
Some websites are created specifically to spread malware, while others are normal sites that have been hacked. These sites may display false update messages, offer fake tools, or show pop-ups asking you to install so-called codecs or fixes.
They can also use drive-by downloads, where the site quietly abuses a flaw in your browser or plugin. If your system is not fully updated, simply visiting such a site can be enough for spyware to be installed.
Software Bundles
Spyware is often included with other software, especially free programs. During installation, the setup process may add extra components such as toolbars, advertising software, or tracking modules.
These additions are sometimes pre-selected or only mentioned in small text. If you move quickly through the installation and accept the default options, you may install these unwanted components, including spyware, without noticing.
Fake Apps or Software
Fake or untrusted applications are a common source of app spyware, particularly on mobile devices and third-party download sites. Examples include copies of popular apps that are not from the official publisher, free utilities that ask for permissions they do not need, and cracked or pirated software that hides Trojans.
Once installed, these apps can use their permissions to monitor your activity or to place more malicious software on your device.
Infected Attachments and Zero-Day Attacks
Spyware can also be delivered through attachments in emails or messages, such as documents, images, or archive files.
Opening these files can trigger hidden code that installs spyware, especially if your system or applications are out of date. In more targeted cases, attackers may use previously unknown security flaws, known as zero-day vulnerabilities, to install spyware without any visible action from you.
What Problems Spyware Can Cause
Data Theft and Identity Theft
Spyware can steal logins, card details, and other personal data. Attackers can then access your accounts, take money, make purchases, or open credit in your name. Fixing identity theft is often slow and stressful.
Slow Device Performance
Spyware runs in the background and uses your device’s memory, processor, and internet connection. As the load increases, apps may open more slowly, freeze during use, or cause the whole system to crash. On phones and tablets, this constant activity can also drain the battery faster than normal and lead to unusually high mobile data usage.
Unauthorized Changes
To stay on the device, spyware often changes settings without telling you. It might replace your homepage or search engine, install extra toolbars or extensions, or lower security settings and turn off updates. These changes make the device less secure and increase the risk of further infections over time.
Browser Hijacking and Pop-up Ads
Some spyware and adware interfere directly with your browser. They can redirect you to unwanted or unsafe websites, alter search results so you see certain pages first, and display frequent pop-up ads. This behaviour interrupts normal browsing and exposes you to more scams, phishing attempts, and other malicious content.
Wider Impact
When spyware is used to monitor journalists, activists, lawyers, or political opponents, it can expose confidential contacts, harm freedom of expression, and put people at real risk. For this reason, highly invasive spyware is treated as both a security and a human rights issue.
Signs You Might Have Spyware
Computer spyware is designed to be hidden, but it often causes side effects. Common signs include:
- Your device is slower than usual or crashes more often
- You see many pop-up ads, even on websites that normally do not show them
- Your homepage, search engine, or other browser settings change without your action
- New apps, programs, toolbars, or icons appear that you do not recognise
- On mobile, your battery drains quickly and data usage is higher than expected
These symptoms can have other causes, but if several appear together, it is sensible to suspect spyware and check the device.
How to Remove Spyware
If you think your device may be infected with spyware, take the following steps.
Run a Full Security Scan
Use reputable antivirus or anti-spyware software and run a complete scan. Allow it to remove or quarantine any threats it finds.
Uninstall Suspicious Software
Check your installed apps and programs. Remove anything you do not recognise, no longer need, or did not intend to install. On browsers, remove unknown extensions and toolbars.
Reset Browser Settings
Reset your homepage, search engine, and other key settings to trusted defaults.
Update Your System and Apps
Make sure your operating system, browser, and important applications are fully updated. Security patches close many of the holes that spyware uses.
Change Your Passwords
After cleaning the device, change passwords for important accounts such as email, banking, and social media. Do this from a device you trust, if possible. Enable two-factor authentication where available.
Consider a Reset or Reinstall
If spyware keeps returning, or if you suspect a deep infection, back up important files and consider a factory reset (on mobile devices) or a clean reinstall of the operating system (on computers). Only reinstall software and restore data from trusted sources.
If you believe you are being intentionally targeted because of your work or role, seek help from a trusted digital security organisation or professional before wiping the device.
How to Protect Yourself From Spyware
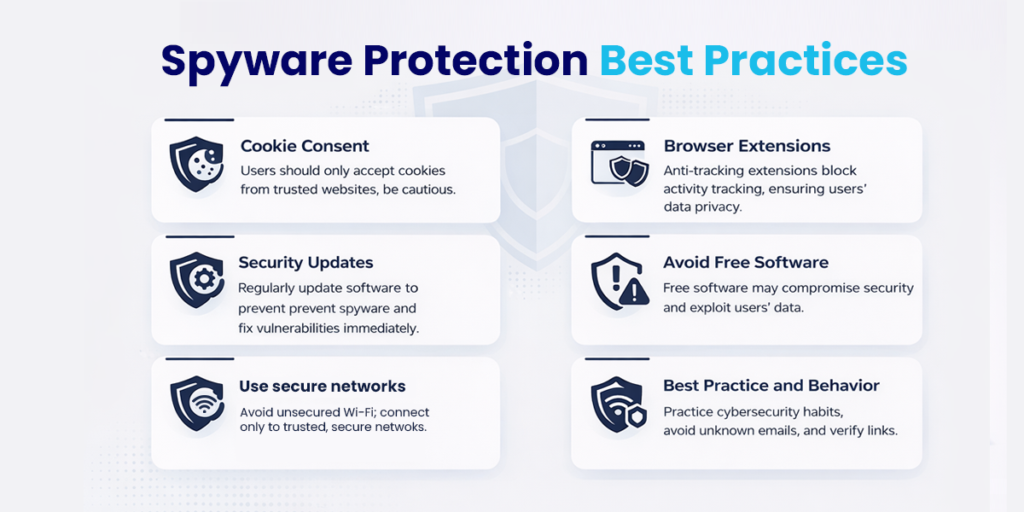
Preventing spyware is easier than removing it, and it is an important part of computer virus protection. Here are steps you can take to protect yourself:
- Using trusted security software with real-time protection and keeping it updated
- Keeping your operating system, browsers, and apps up to date
- Only downloading software and apps from official websites and app stores
- Being careful with email links and attachments, especially from unknown or unexpected senders
- Using strong, unique passwords for each account and enabling two-factor authentication
- Regularly reviewing app permissions on mobile devices and limiting access to the camera, microphone, location, SMS, and contacts
A firewall can help control network connections. When using public Wi-Fi, a trusted VPN can protect your connection. Note that a VPN does not remove spyware that is already installed; it only helps protect your traffic on the network.
Final Thoughts
Spyware is a serious issue that can harm your privacy, steal your personal data, and affect how your device works. Knowing how it spreads, what signs to watch for, and how to remove or prevent it can help you stay protected.
Using trusted security software, being careful with downloads and links, and keeping your device updated are simple but effective ways to stay safe. Staying alert and informed is the best way to avoid spyware.
FAQs
How can I know if spyware is on my device?
You cannot be sure without a security scan, but signs include slow performance, crashes, pop-ups, changed browser settings, unknown apps or toolbars, fast battery drain, and unexplained data usage. If you notice several of these, run a full scan with trusted security software.
Can spyware infect iPhones and Android phones?
Yes. Both iPhones and Android devices can be infected with mobile spyware that can track your location, read messages, see call logs, and access files. Keeping the system updated and using only official app stores helps reduce the risk.
Is all spyware harmful?
In cybersecurity, “spyware” usually means software that collects information without proper consent and is treated as harmful or unwanted. Monitoring tools used openly with clear policies are different, but if the same tools are used secretly or to control someone, they are considered spyware or stalkerware.
What should I do if I think I have spyware?
Run a scan with reputable security software, remove or quarantine any threats, uninstall suspicious apps or programs, update your system, and change passwords for important accounts. If the problem continues, seek professional help and consider resetting or reinstalling the device.
How can I stop spyware from infecting my device?
Use reliable security software, keep your system and apps updated, download only from trusted sources, be careful with email links and attachments, use strong unique passwords with two-factor authentication, and regularly review app permissions on your phone. These habits greatly lower the chance of infection.


Comments are closed